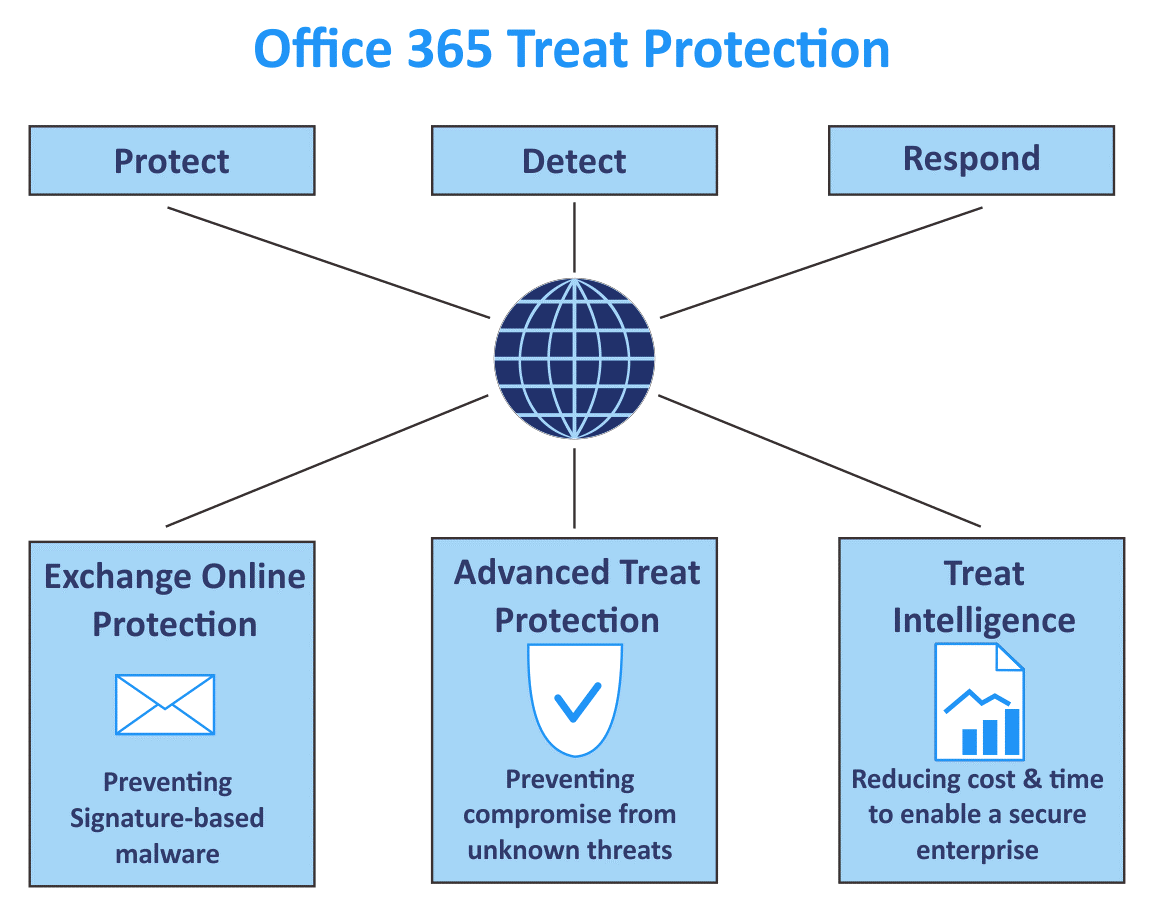
Microsoft Defender per Office 365 è un servizio di filtro della posta elettronica basato su cloud che consente di proteggere l'organizzazione da malware e virus sconosciuti fornendo una protezione zero-day affidabile e include funzionalità per proteggere l'organizzazione da collegamenti dannosi in tempo reale.Microsoft Defender for Office 365 is a cloud-based email filtering service that helps protect your organization against unknown malware and viruses by providing robust zero-day protection, and includes features to safeguard your organization from harmful links in real time.Defender per Office 365 include funzionalità avanzate di creazione di report e traccia url che consentono agli amministratori di comprendere il tipo di attacchi che si verificano nell'organizzazione.Defender for Office 365 has rich reporting and URL trace capabilities that give administrators insight into the kind of attacks happening in your organization.
Office 365 allows you to enable this feature as well. ATP Safe Links features are part of Advanced Threat Protection, which is included in Office 365 Enterprise E5, Microsoft 365 Business. ORCA is a project to help Office 365 tenant administrators validate their anti-spam and anti-malware settings against recommendations from Microsoft. ORCA is installed as a PowerShell module with just one cmdlet. After running Get-ORCAReport, you’ll have a report containing recommendations and obs.
Automated incident response (AIR) capabilities available in Office 365 ATP Plan 2 enable you to run automated investigation processes in response to well known threats that exist today. By automated certain investigation tasks, your security operations team can operate more efficiently and effectively.
Di seguito sono riportati i modi principali per usare Defender per Office 365 per la protezione dei messaggi:The following are the primary ways you can use Defender for Office 365 for message protection:
In uno scenario di solo filtro di Defender per Office 365, Defender per Office 365 fornisce la protezione della posta elettronica basata su cloud per l'ambiente Exchange Server locale o qualsiasi altra soluzione di posta elettronica SMTP locale.In a Defender for Office 365 filtering-only scenario, Defender for Office 365 provides cloud-based email protection for your on-premises Exchange Server environment or any other on-premises SMTP email solution.
Defender per Office 365 può essere abilitato per proteggere le cassette postali ospitate sul cloud di Exchange Online.Defender for Office 365 can be enabled to protect Exchange Online cloud-hosted mailboxes.Per ulteriori informazioni su Exchange Online, vedere la descrizione del servizio Exchange Online.To learn more about Exchange Online, see the Exchange Online service description.
In una distribuzione ibrida, Defender per Office 365 può essere configurato per proteggere l'ambiente di messaggistica e controllare il routing della posta quando si dispone di una combinazione di cassette postali locali e cloud con Exchange Online Protection per il filtro della posta elettronica in ingresso.In a hybrid deployment, Defender for Office 365 can be configured to protect your messaging environment and control mail routing when you have a mix of on-premises and cloud mailboxes with Exchange Online Protection for inbound email filtering.
Disponibilità di Microsoft Defender per Office 365Microsoft Defender for Office 365 availability
Microsoft Defender per Office 365 Piano 2 è incluso in Office 365 E5, Office 365 A5, Microsoft 365 E5 Security e Microsoft 365 E5 come specificato qui: https://docs.microsoft.com/microsoft-365/security/office-365-security/office-365-atp .Microsoft Defender for Office 365 Plan 2 is included in Office 365 E5, Office 365 A5, Microsoft 365 E5 Security, and Microsoft 365 E5 as specified here: https://docs.microsoft.com/microsoft-365/security/office-365-security/office-365-atp.Defender per Office 365 Piano 1 è incluso in Microsoft 365 Business Premium.Defender for Office 365 Plan 1 is included in Microsoft 365 Business Premium.
È possibile aggiungere Defender per Office 365 ai seguenti piani di sottoscrizione di Exchange e Microsoft 365:You can add Defender for Office 365 to the following Exchange and Microsoft 365 subscription plans:
Exchange Online Piano 1Exchange Online Plan 1
Exchange Online, piano 2Exchange Online Plan 2
Chiosco Exchange OnlineExchange Online Kiosk
Exchange Online ProtectionExchange Online Protection
Microsoft 365 Business BasicMicrosoft 365 Business Basic
Microsoft 365 Business StandardMicrosoft 365 Business Standard
Office 365 Enterprise E1Office 365 Enterprise E1
Office 365 Enterprise E3Office 365 Enterprise E3
Office 365 Enterprise F3Office 365 Enterprise F3
Office 365 A1Office 365 A1
Office 365 A3Office 365 A3
Per acquistare Microsoft Defender per Office 365, vedere Microsoft Defender per Office 365.To buy Microsoft Defender for Office 365, see Microsoft Defender for Office 365.
Per informazioni dettagliate sui piani sulle sottoscrizioni che consentono agli utenti di Microsoft Defender per Office 365, vedere la tabella di confronto completa delle sottoscrizioni.For detailed plan information on subscriptions that enable users for Microsoft Defender for Office 365, see the full subscription comparison table.

Novità di Microsoft Defender per Office 365What's new in Microsoft Defender for Office 365
Stiamo continuando ad aggiungere nuove funzionalità a Defender per Office 365.We are continuing to add new features to Defender for Office 365.Per altre informazioni sulle nuove funzionalità disponibili in Defender per Office 365 (o Microsoft 365 in generale), vedere le risorse seguenti:To learn more about new features coming to Defender for Office 365 (or Microsoft 365 in general), see the following resources:
Requisiti per Microsoft Defender per Office 365Requirements for Microsoft Defender for Office 365
Defender per Office 365 può essere utilizzato con qualsiasi agente di trasferimento della posta SMTP, ad esempio Microsoft Exchange Server.Defender for Office 365 can be used with any SMTP mail transfer agent, such as Microsoft Exchange Server.Per informazioni sui sistemi operativi, i Web browser e le lingue supportati da Defender per Office 365, vedere le sezioni 'Browser supportati' e 'Lingue supportate' nell'interfaccia di amministrazione di Exchange in Exchange Online Protection.For information about the operating systems, web browsers, and languages that are supported by Defender for Office 365, see the 'Supported browsers' and 'Supported languages' sections in Exchange admin center in Exchange Online Protection.
Disponibilità delle funzionalità tra i piani di Defender per Office 365Feature availability across Defender for Office 365 plans
Di seguito sono elencate tutte le funzionalità. Quando è menzionato Exchange Online, in genere si intende la famiglia di servizi di Office 365 Enterprise.Each feature is listed below. When Exchange Online is mentioned, it typically refers to the Office 365 Enterprise service family.
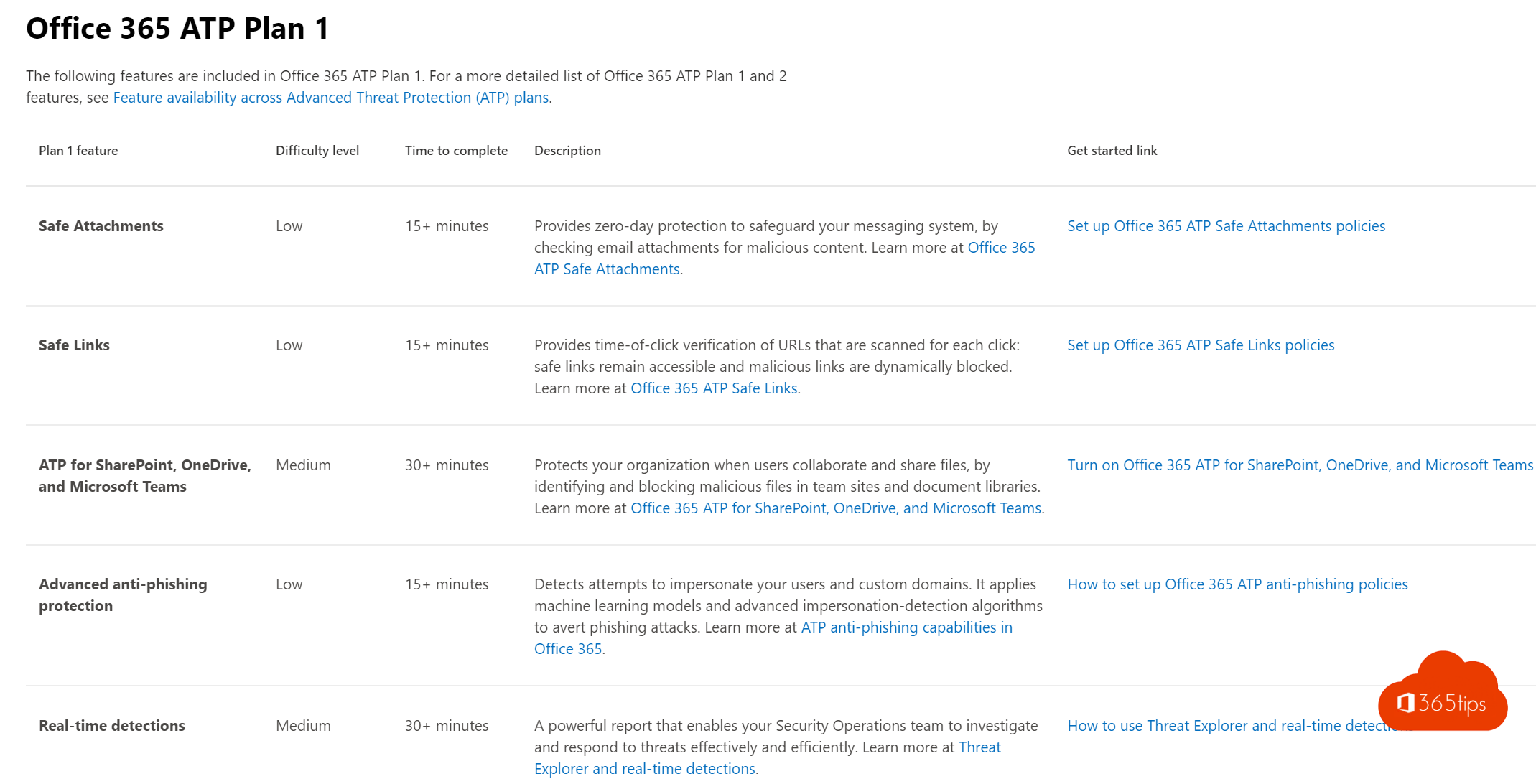
| FunzionalitàFeature | Defender per Office 365 Piano 1Defender for Office 365 Plan 1 | Defender per Office 365 Piano 2Defender for Office 365 Plan 2 | Microsoft 365 E5 / A5 SecurityMicrosoft 365 E5 / A5 Security |
|---|---|---|---|
| Configurazione, protezione e rilevamentoConfiguration, protection, and detection | |||
| Allegati sicuriSafe Attachments | SìYes | SìYes | SìYes |
| Allegati sicuri in TeamsSafe Attachments in Teams | SìYes | SìYes | SìYes |
| Collegamenti sicuriSafe Links | SìYes | SìYes | SìYes |
| Sicurezza documentiSafe Documents | NoNo | NoNo | SìYes |
| Collegamenti sicuri in TeamsSafe Links in Teams | SìYes | SìYes | SìYes |
| ATP per SharePoint, OneDrive e Microsoft TeamsATP for SharePoint, OneDrive, and Microsoft Teams | SìYes | SìYes | SìYes |
| Criteri anti-phishingAnti-phishing policies | SìYes | SìYes | SìYes |
| Report in tempo realeReal-time reports | SìYes | SìYes | SìYes |
| Automazione, indagine, correzione ed istruzioneAutomation, investigation, remediation, and education | |||
| Tracker delle minacceThreat Trackers | NoNo | SìYes | SìYes |
| Indagine sulle minacce (indagine avanzata sulle minacce)Threat investigation (advanced threat investigation) | Rilevamenti in tempo realeReal-time detections | ExplorerExplorer | ExplorerExplorer |
| Risposta automatica agli eventi imprevistiAutomated incident response | NoNo | SìYes | SìYes |
| Simulatore di attacchiAttack Simulator | NoNo | SìYes | SìYes |
| Integrazione con Microsoft 365 DefenderIntegration with Microsoft 365 Defender | NoNo | SìYes | SìYes |
Nota
Se il tenant dispone solo della licenza di valutazione di Microsoft Defender per Office Plan P2 o office 365 E5, senza altre licenze idonee per Microsoft 365 Defender, non sarà possibile accedere a Microsoft 365 Defender.If your tenant only has Microsoft Defender for Office Plan P2 trial license or Office 365 E5 trial license, with no other eligible license for Microsoft 365 Defender, you will not be able to access Microsoft 365 Defender.Per altre informazioni sulla licenza MTP, vedi Requisiti di Microsoft 365 Defender.To learn more about MTP license, see Microsoft 365 Defender requirements.
Funzionalità di Defender per Office 365Defender for Office 365 capabilities
Allegati sicuriSafe Attachments
Gli allegati sicuri proteggono da malware e virus sconosciuti e forniscono una protezione zero-day per proteggere il sistema di messaggistica.Safe Attachments protects against unknown malware and viruses, and provides zero-day protection to safeguard your messaging system.Tutti i messaggi e gli allegati che non dispongono di una firma virus/malware nota vengono instradati a un ambiente speciale in cui Defender per Office 365 usa un'ampia gamma di tecniche di apprendimento automatico e analisi per rilevare intenti dannosi.All messages and attachments that don't have a known virus/malware signature are routed to a special environment where Defender for Office 365 uses a variety of machine learning and analysis techniques to detect malicious intent.Se non viene rilevata alcuna attività sospetta, il messaggio viene rilasciato per il recapito alla cassetta postale.If no suspicious activity is detected, the message is released for delivery to the mailbox.
Nota
L'analisi degli allegati sicuri avviene nella stessa area in cui si trovano i dati di Office 365.Safe Attachments scanning takes place in the same region where your Office 365 data resides.Per ulteriori informazioni sull'area geografica del data center, vedere Dove si trovano i dati?For more information about data center geography, see Where is your data located?
Collegamenti sicuriSafe Links
La funzionalità Collegamenti sicuri protegge in modo proattivo gli utenti da URL dannosi in un messaggio o in un documento di Office.The Safe Links feature proactively protects your users from malicious URLs in a message or in an Office document.La protezione rimane attiva ogni volta che l'utente seleziona il collegamento, perché i collegamenti dannosi vengono bloccati in modo dinamico mentre i collegamenti corretti continuano ad essere accessibili.The protection remains every time they select the link, as malicious links are dynamically blocked while good links can be accessed.
I collegamenti sicuri sono disponibili per gli URL nelle seguenti app:Safe Links is available for URLs in the following apps:
Microsoft 365 Apps for enterprise in Windows o MacMicrosoft 365 Apps for enterprise on Windows or Mac
Office per il Web (Word per il Web, Excel per il Web, PowerPoint per il Web e OneNote per il Web)Office for the web (Word for the web, Excel for the web, PowerPoint for the web, and OneNote for the web)
Word, Excel e PowerPoint in WindowsWord, Excel, and PowerPoint on Windows
Canali e chat di Microsoft TeamsMicrosoft Teams channels and chats
Nota
Gli utenti devono disporre di una licenza per Defender per Office 365, devono essere inclusi nei criteri collegamenti sicuri e devono accedere ai propri dispositivi perché la protezione sia * in atto.Users must be licensed for Defender for Office 365*, must be included in Safe Links policies, and must be signed in on their devices for protection to be in place.
* Per le licenze di Defender per Office 365 a livello di organizzazione (ad esempio, ATP_ENTERPRISE_FACULTY), non è necessario assegnare le licenze defender per Office 365 ai singoli utenti.* For organization-wide Defender for Office 365 licenses (for example, ATP_ENTERPRISE_FACULTY), you don't need to assign Defender for Office 365 licenses to individual users.
Per ulteriori informazioni sulla protezione dei collegamenti sicuri, vedere Collegamenti sicuri in Microsoft Defender per Office 365.For more information about Safe Links protection, see Safe Links in Microsoft Defender for Office 365.
Sicurezza documentiSafe Documents
La funzionalità Documenti sicuri usa Microsoft Defender for Endpoint per analizzare i documenti e i file aperti in Visualizzazione protetta.The Safe Documents feature uses Microsoft Defender for Endpoint to scan documents and files that are opened in Protected View.
Che cosa è necessario sapere prima di iniziareWhat do you need to know before you begin?
Documenti sicuri è ora disponibile in genere per gli utenti con Office versione 2004 (12730.x) o versione successiva.Safe Documents is now generally available to users with Office Version 2004 (12730.x) or greater!Questa funzionalità è disattivata per impostazione predefinita e dovrà essere abilitata dall'amministratore della sicurezza.This feature is off by default and will need to be enabled by the Security Administrator.
Questa funzionalità è disponibile solo per gli utenti con la licenza Microsoft 365 E5 o Microsoft 365 E5 Security (non inclusa nei piani Defender per Office 365).This feature is only available to users with the Microsoft 365 E5 or Microsoft 365 E5 Security license (not included in Defender for Office 365 plans).
Word, Excel e PowerPoint in WindowsWord, Excel, and PowerPoint on Windows
Canali e chat di Microsoft TeamsMicrosoft Teams channels and chats
Nota
Gli utenti devono disporre della licenza per Microsoft 365 E5 o Microsoft 365 E5 Security, devono essere inclusi nei criteri Documenti sicuri e devono essere connessi ai propri dispositivi per consentire la * protezione.Users must be licensed for Microsoft 365 E5 or Microsoft 365 E5 Security*, must be included in Safe Documents policies, and must be signed in on their devices for protection to be in place.
Per ulteriori informazioni sulla protezione dei documenti sicuri, vedere Documenti sicuri in Microsoft 365 E5.For more information about Safe Documents protection, see Safe Documents in Microsoft 365 E5.
ATP per SharePoint, OneDrive e Microsoft TeamsATP for SharePoint, OneDrive, and Microsoft Teams
Working on demo. ATP per SharePoint, OneDrive e Microsoft Teams consente di rilevare e bloccare i file identificati come dannosi nei siti del team e nelle raccolte documenti.ATP for SharePoint, OneDrive, and Microsoft Teams helps detect and block files that are identified as malicious in team sites and document libraries.Inoltre, la protezione dei collegamenti sicuri è ora disponibile nei canali e nelle chat di Microsoft Teams.In addition, Safe Links protection is now available in Microsoft Teams channels and chats.
Criteri anti-phishingAnti-phishing policies
Anti-phishing controlla la presenza di indicatori che un messaggio potrebbe essere un tentativo di phishing nei messaggi in arrivo.Anti-phishing checks incoming messages for indicators that a message might be a phishing attempt.Quando gli utenti sono coperti dai criteri di Defender per Office 365 (allegati sicuri, collegamenti sicuri o anti-phishing), i messaggi in arrivo vengono valutati da più modelli di machine learning che analizzano i messaggi e viene eseguita l'azione appropriata, in base ai criteri configurati.When users are covered by Defender for Office 365 policies (Safe Attachments, Safe Links, or anti-phishing), incoming messages are evaluated by multiple machine learning models that analyze messages and the appropriate action is taken, based on the configured policies.
Report in tempo realeReal-time reports
Le funzionalità di monitoraggio disponibili nel Centro sicurezza & e conformità ( ) includono report e informazioni dettagliate in tempo reale che consentono agli amministratori di sicurezza e conformità di concentrarsi su problemi ad alta priorità, ad esempio attacchi alla sicurezza o attività https://protection.office.com sospette. Monitoring capabilities available in the Security & Compliance Center (https://protection.office.com) include real-time reports and insights that let your security and compliance administrators focus on high-priority issues, such as security attacks or increased suspicious activity.Oltre ad evidenziare le aree di problema, i report intelligenti e le informazioni dettagliate includono suggerimenti e collegamenti per visualizzare ed esplorare i dati ed eseguire azioni rapide.In addition to highlighting problem areas, smart reports and insights include recommendations and links to view and explore data and also take quick actions.
ExplorerExplorer
Explorer (anche noto come Esplora minacce) è un report in tempo reale che consente agli utenti autorizzati di identificare e analizzare le minacce recenti.Explorer (also referred to as Threat Explorer) is a real-time report that lets authorized users identify and analyze recent threats.Per impostazione predefinita, questo report mostra i dati degli ultimi sette giorni. Tuttavia, le visualizzazioni possono essere modificate per visualizzare i dati degli ultimi 30 giorni.By default, this report shows data for the past seven days; however, views can be modified to show data for the past 30 days.
Explorer contiene visualizzazioni, ad esempio Malware (per posta elettronica e contenuto), Invii, Phish e Tutti i messaggi di posta elettronica.Explorer contains views, such as Malware (for email and content), Submissions, Phish, and All Email.Per vedere il confronto tra Esplora risorse e i rilevamenti in tempo reale, scarica questo PDF.To see how Explorer compares with real-time detections, download this PDF.
Per ulteriori informazioni su Explorer (in Microsoft Defender per Office 365 Piano 2) e sui rilevamenti in tempo reale (in Microsoft Defender per Office 365 Piano 1), vedere Threat Explorer e rilevamenti in tempo reale.For more information about Explorer (in Microsoft Defender for Office 365 Plan 2) and real-time detections (in Microsoft Defender for Office 365 Plan 1), see Threat Explorer and real-time detections. Google docs app for windowsselfiequiet.
Rilevamenti in tempo realeReal-time detections
I rilevamenti in tempo reale consentono agli utenti autorizzati di identificare e analizzare le minacce recenti.Real-time detections is a real-time report that lets authorized users identify and analyze recent threats.Analogamente a Explorer, per impostazione predefinita, questo report mostra i dati degli ultimi sette giorni.Similar to Explorer, by default, this report shows data for the past seven days.
I rilevamenti in tempo reale contengono visualizzazioni, ad esempio Malware (per posta elettronica e contenuto), Invii e Phish.Real-time detections contain views, such as Malware (for email and content), Submissions, and Phish.Per vedere come vengono confrontati i rilevamenti in tempo reale con Explorer, scarica questo PDF.To see how real-time detections compare with Explorer, download this PDF.
Per ulteriori informazioni su Explorer (in Microsoft Defender per Office 365 Piano 2) e sui rilevamenti in tempo reale (in Microsoft Defender per Office 365 Piano 1), vedere Threat Explorer (erilevamenti in tempo reale).For more information about Explorer (in Microsoft Defender for Office 365 Plan 2) and real-time detections (in Microsoft Defender for Office 365 Plan 1), see Threat Explorer (and real-time detections).

Tracker delle minacceThreat Trackers
I tracker delle minacce sono widget informativi e visualizzazioni che forniscono agli utenti autorizzati informazioni sui problemi di cybersecurity che potrebbero influire sull'organizzazione.Threat Trackers are informative widgets and views that provide authorized users with intelligence on cybersecurity issues that might impact your organization.
Risposta automatica agli eventi imprevistiAutomated incident response
Le funzionalità AIR (Automated Incident Response) disponibili in Defender per Office 365 Piano 2 consentono di eseguire processi di indagine automatizzati in risposta alle minacce note attualmente esistenti.Automated incident response (AIR) capabilities available in Defender for Office 365 Plan 2 let you run automated investigation processes in response to well-known threats that exist today.Automatizzando determinate attività di indagine, il team delle operazioni di sicurezza può operare in modo più efficiente ed efficace.By automated certain investigation tasks, your security operations team can operate more efficiently and effectively.Le azioni di correzione, ad esempio l'eliminazione di messaggi di posta elettronica dannosi, vengono intraprese dopo l'approvazione da parte del team delle operazioni di sicurezza.Remediation actions, such as deleting malicious email messages, are taken upon approval by your security operations team.Per ulteriori informazioni, vedere Funzionamento di AIR in Office 365.To learn more, see How AIR works in Office 365.
Simulatore di attacchiAttack Simulator
Il simulatore di attacco consente agli utenti autorizzati di eseguire scenari di attacco realistici nell'organizzazione.Attack Simulator lets authorized users run realistic attack scenarios in your organization.Sono disponibili diversi tipi di attacchi, tra cui un attacco di spear-phishing con nome visualizzato, un attacco di tipo password spray e un attacco con password di forza bruta.Several different kinds of attacks are available, including a display name spear-phishing attack, a password-spray attack, and a brute-force password attack.
Cybersecurity Ventures, a computer and network security organization in California has predicted that by the end of 2022, the number of internet users would be around 6 billion. It roughly translates to about 75 percent of the total world population. Everyone is moving towards the digital era and welcoming the latest technology with both hands. But still, some organizations are yet to upgrade their security posture to defend against the latest security threats.
On the other hand, cybercriminals are also welcoming the growing trend of digitalization. More users mean more targets for them, and they take advantage of the development in mainstream IT to hone their craft. As a result, cybercrimes like phishing have evolved into a significant issue for everyone, including small, midsized, and even huge corporate firms, too. Although organizations are deploying sophisticated measures to protect themselves from these threats, success depends on the human resource – the employees who are the end-users in every enterprise. It is estimated that 90 percent of the security breaches that happen in enterprises across the globe is because of a human error. Employees expose their credentials or other sensitive information by clicking on malicious links or downloading harmful attachments.
This is where Microsoft’s Advanced Threat Protection for Office 365 can play a massive role in protecting its users and their online applications – emails and data – using intelligent solutions.
Office 365 Phishing Protection
Microsoft Office 365 Advanced Threat Protection is an advanced email filtering service hosted on the cloud. It provides a complete cover for organizations from malware, virus, and other phishing attacks.
Its unique zero-day protection feature provides enterprises with real-time analysis and protection from malicious links. It also comes equipped with a unique URL tracing feature that allows administrators to monitor all kinds of linked URLs to prevent attacks and penetrations happening inside the organization.
Some of the features provided by Microsoft’s Advanced Threat Protection are as given below:
Safe Links
One of the significant highlights of Office 365 phishing protection is the safe links feature. It offers the ultimate security against all kinds of malicious links in your emails and other office documents.
The ATP is built similarly to the firewalls used for web-protection. It provides a protection feature called time-of-click verification of URLs. What this means is that when the recipient clicks on a link, the ATP scans and analyzes the URL to which the link leads before allowing the web page to open. It allows safe URLs to open but dynamically blocks phishing websites and suspicious URLs.
Safe Attachments
Newly launched malware and viruses can easily bypass anti-virus software and other scanning engines because the filters and scanners do not have anything in their databases to detect these. The anti-virus software or filter need to classify them and upload their virus signatures into their filter databases first. Only then can they identify and block these viruses and the attachments containing them.
But with the Microsoft Office Advanced Threat Protection, a malicious email does not enter the user’s inbox just because the existing database does not see it as suspicious. The office 365 ATP anti-phishing checks every email for unsafe attachment. It blocks the known threats and quarantines all other emails in a sandboxed virtual environment. There, it uses AI and machine learning to analyze their contents and continuously monitors the emails and their attachments. It releases each email to the user’s inbox only if it detects no suspicious activity and considers the email to be safe.
Spoof Intelligence
Spoof intelligence is another highlight of the Advanced Threat Protection software that helps in detecting spoof emails. The feature continuously monitors all incoming emails and those that are circulating within the organization. With the spoof intelligence feature, the ATP enables the users to quickly detect spoofing of domains that belong to them as well as that of external domains.
The consequences of having your domain spoofed can be severe because the sender can send just about anything in your name. However, businesses may also have genuine requirements of spoofing, such as when an enterprise hires an external firm to manage its marketing campaigns. The ATP caters to both malicious and legitimate spoofing by allowing the user to either block the sender or take no action. Whatever the case may be, the ATP’s spoof intelligence will detect any spoofing and leave it at the user’s hands to deal with it.
Anti-Phishing Policies
Microsoft ATP has default policies that apply to all the Office 365 users. However, the users can customize these based on their requirements and organization environment. The customized policies then take precedence over the default ones. The users can also edit, delete, or add to the policies whenever the need arises. Enterprises can customize or make changes to their policies easily from the Office 365 Security & Compliance Center.
Real-Time Reports
Microsoft Advanced Threat Protection provides an advanced reporting dashboard that allows administrators to view the performance of the ATP in the form of reports. Some of the report formats available in the ATP include:
- Threat Explorer
- Threat Protection Status Report
- ATP File Types Report
- ATP Message Disposition Report

O365 Atp
Exchange Online Advanced Threat Protection
O365 Atp Api
Organizations can deploy the Office 365 phishing protection and the Advanced Threat Protection to support their applications across multiple platforms. Users of any SMTP mail transfer agent, like the Microsoft Exchange Server, can use the ATP’s protection. This cross-platform usability means that you can use the ATP as Exchange online advanced threat protection.
Conclusion
The Microsoft Office 365 phishing protection uses Artificial Intelligence and machine learning models to study the environment and adapt itself based on how the organization utilizes data. It is not a universal solution to protect against all kind of malicious attacks. But it is undoubtedly a great tool to provide security against unknown viruses and malware.
For flexible per-user pricing, PhishProtection’s integrated email security solution protects your employees from business email compromise (BEC) and many other email threats. 24×7. On any device. With features you’d expect in more expensive solutions:
All Plans Come With
- Stops business email compromise (BEC)
- Stops brand forgery emails
- Stop threatening emails before they reach the inbox
- Continuous link checking
- Real-time website scanning
- Real time alerts to users and administrators
- Protection with settings you control
- Protection against zero day vulnerabilities
- Complete situational awareness from web-based console
O365 Atp P1 Pricing
Phish Protection works with System Administrators, IT Professionals and IT Executives in thousands of companies worldwide. Sign up and protect your organization from phishing attacks in less than 5 minutes
Carbon C-14 is an unstable isotope of carbon created when a neutron collides with a nitrogen atom, causing capture of the neutron and release of the proton converting nitrogen to a carbon with fourteen nucleons (6 protons and 8 neutrons). Carbon-14 emits beta particles as. Silicon is a chemical element with atomic number 14 which means there are 14 protons and 14 electrons in the atomic structure. The chemical symbol for Silicon is Si. Silicon is a hard and brittle crystalline solid with a blue-grey metallic lustre, it is a tetravalent metalloid and semiconductor. Carbon 13 atomic number proton neutron. Isotopes are atoms with the same atomic number Z and a different mass number (A). That is, they differ in the number of neutrons (eg carbon 12, has 6 protons, 6 electrons, and 6 neutrons,and carbon 14, 8 neutrons, 6 electrons, and 6 protons). Carbon-14 (146 C) isotope is unstable and radioactive. Carbon-14 decays by emitting beta particles and giving nitrogen. Carbon-14 is an isotope of carbon. It is written as 146 C.
